We've built a zero-trust world that runs entirely on trust.
Every security system — whether it's your device fleet, customer platform, or payments pipeline — requires humans to trust that the verification works, that the policies make sense, and that the friction has a purpose. When this trust breaks, security fails.
Security isn't a software setting. It's a social contract, enforced by technical boundaries. The irony is that while we architect "never trust, always verify" systems, we're asking people to place absolute trust in those very systems. This paradox sits at the heart of why so many security initiatives fail.
Consider this scenario: A retail company equips every store associate with a locked-down tablet for inventory management and customer checkout. The devices are configured with strict application controls — only approved point-of-sale and inventory apps can run. It's a textbook zero-trust implementation.
Then Black Friday approaches. The inventory app starts crashing under load. Associates can't check stock levels. Customers are waiting. A tech-savvy employee remembers that the previous version of the app — before last month's mandatory security update — never had these stability issues. They find a way to sideload the old APK through developer mode (the password was on a sticky note in the manager's office — right next to the mandatory security awareness poster). Sure, IT said the old version had "critical security vulnerabilities," but what's the bigger risk: theoretical hackers or actual customers walking out angry enough to leave one-star reviews? Word spreads. By Monday, half the fleet is running the outdated, vulnerable version.
The company's response? Lock down developer mode harder. Add more monitoring. Create harsher penalties. But they've missed the real failure: the moment employees chose workarounds over approved tools, trust was already broken. No amount of additional verification can fix a trust relationship that's fundamentally severed.
The Trust Paradox in Zero-Trust Security
Security is most often considered in terms of its constituent components, not its holistic outcomes. Policies, passwords, tools, and controls act as a series of locked gates, each attesting to the user's identity, intent, and overall trustworthiness. But here's where zero-trust thinking hits a wall: those gates only work if people trust them enough to use them properly.
When we really consider that word — trustworthiness — we need to ask ourselves: Do my locked gates actually enable systemic trust, or do they merely act as a series of rules that people navigate around?
The zero-trust model says "verify everything," but it can't verify whether your employees believe in the system. It can't verify whether they'll share passwords when deadlines loom. It can't verify whether they'll prop open secure doors or install shadow IT to "get real work done."
But how do we build this human trust layer? The answer isn't "more rules" or "more verification." It's the considered and precise application of friction.
Trust is the System. Friction is the Tool.
Friction reinforces trust. It signals that something matters and deserves attention. Whether it's a second-factor prompt for privileged access, a rollback path for risky updates, or a policy that blocks unauthorized app installation, the goal remains the same: Protect trust without creating drag.
Great security teams don't obsess over control. They obsess over clarity. Their job isn't to lock everything down, but to decide where friction belongs and why. Security fails when friction becomes a brick wall or a speed bump — too aggressive to get through, or too subtle to be useful.
And even more important is where that friction is applied: For some doors, a badge-in and an automatic shut are enough. For others, you might need a personally-identifiable rotating keycode. It all depends on what's behind the door, and the risk you're managing when it's opened.
So, while you don't need to ask for an ID, key card, retinal scan, and two-factor code for every locked door, you do need to know which doors actually matter. And not just for the sake of protecting assets and IP, but to build a culture of trust awareness in your organization.
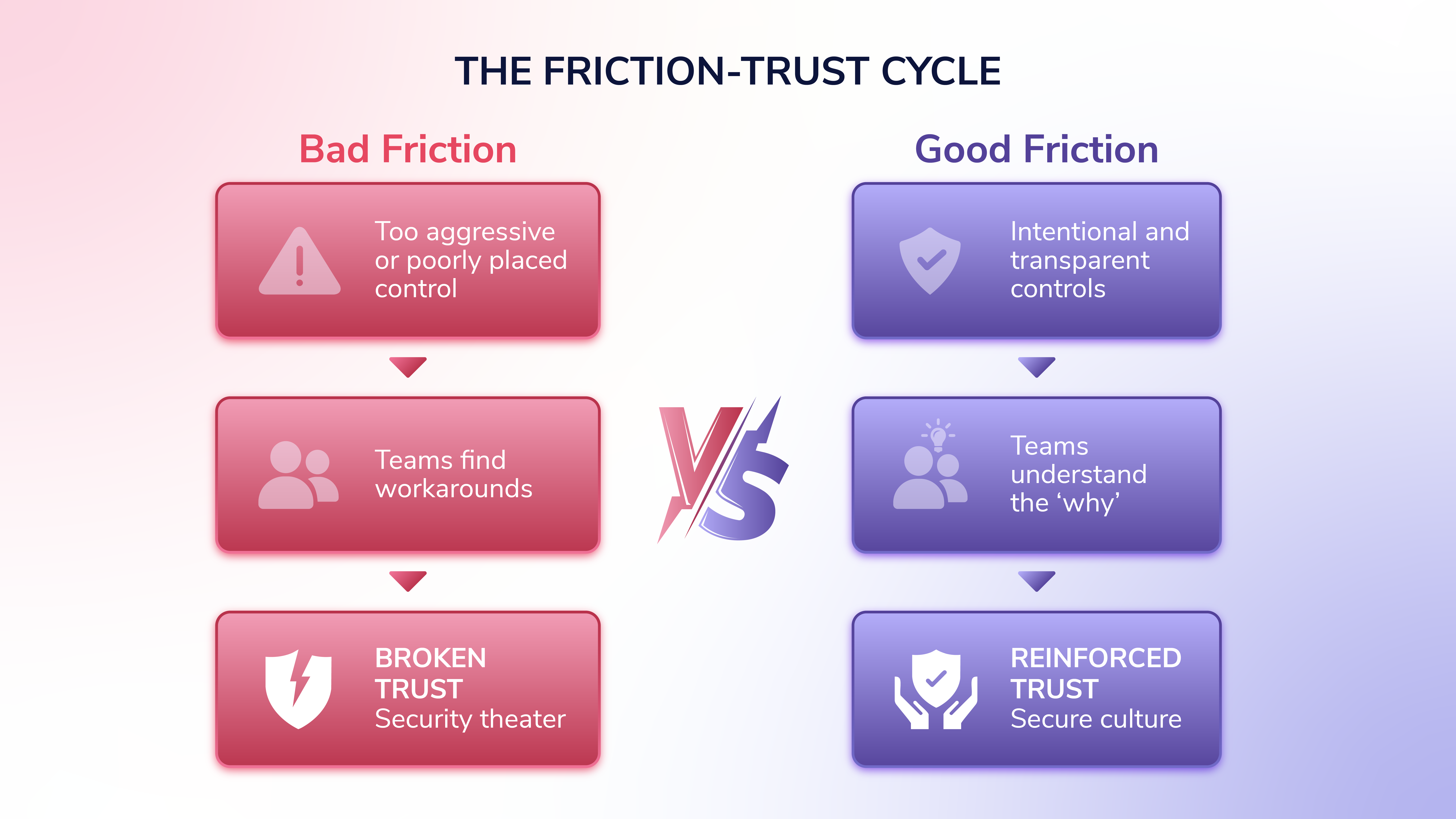
When Zero-Trust Meets Human Reality
Think about this way: If every one of your device settings or content policies needs to be worked around with a supervisor PIN on a daily basis, are your device content policies actually working? A culture of high friction applied monolithically is as bad as one with low friction applied monolithically, because trust isn't a consideration.
Zero-trust architectures excel at technical verification, but they can't verify intent or build culture. When you apply the same friction everywhere — regardless of context or risk — your rules become equally unhelpful. Your employees see them as obstacles rather than safeguards. Soon enough, your perfectly designed zero-trust system becomes elaborate security theater that everyone performs while finding creative ways to get actual work done.
How to Know if Friction is Enabling Secure Outcomes
When you build policies that respect a culture of trust, you're on the right path. But even when you're locking the right doors and applying friction with intention, the proof is in the pudding. Your security is only as strong as your ability to audit it — and not in theory, but in real time. You might assume your policies protect your devices, but proving it is much harder.
That's where friction becomes more than a layer of your security apparatus — it acts as a proactive diagnostic, surfacing drift, rogue updates, and non-compliant devices. If you don't have visibility into where your friction isn't effective, that friction isn't reinforcing trust. It's masking failure.
We all want to believe the boundaries we create through the application of friction are enough on their own. But we equally understand the reality of managing devices and access controls in the field: It's messy. There is a constant flow of escalations and exceptions that lead to misalignment.
Strong trust systems surface that misalignment early. They make the boundaries of your friction visible, not just to IT, but to everyone operating inside them. And they make correction seamless. No guesswork. No manual audit loops. This is where zero-trust principles and human trust converge: transparent verification that people can understand and believe in.
Remember our Black Friday scenario? A trust-based approach would have prevented that breakdown entirely. Instead of forcing updates that degrade performance during critical periods, imagine if you gave store managers official rollback rights — a button in their admin panel that says "Revert to previous version" with a required reason field and automatic re-update after 72 hours. This simple change acknowledges business reality while maintaining security visibility. The manager feels trusted to make the right call for their store. IT gets real-time data about which updates cause problems. Security still happens, just on a timeline that respects operational needs. That's intelligent friction: enough to ensure accountability, not so much that people route around it.
So ask yourself: Is your friction creating clarity? Or is it just hiding a culture of circumvention and compliance avoidance?
What This Means for You
For CISOs: Review your friction points through the trust lens. Map out where you've added security controls and ask whether each one builds or erodes trust. Focus on the ones with the highest circumvention rates first.
For IT Leaders: Ask your teams which policies they work around — and more importantly, why. Create safe channels for this feedback. The answers will show you where your friction has become counterproductive.
For Executives: Stop measuring security by compliance metrics alone. Start asking: How many workarounds exist in our organization? What's our trust score, not just our audit score? These questions reveal your true security posture.
Security Friction Checklist: Test Your Alignment
Here's a 5-step gut check to see whether your device security friction is protecting trust — or just slowing your team down:
1. Can you surface only the devices that are out of policy — without combing through the fleet?
✅ Good friction flags misalignment fast
❌ Bad friction buries it in dashboards
2. Can you stop a risky update before it spreads?
✅ Good friction supports staging and rollback
❌ Bad friction relies on best-case assumptions
3. Do your teams get alerts they can act on?
✅ Good friction is real-time, high-signal
❌ Bad friction is noise that trains them to ignore everything
4. Are users blocked from actions that introduce risk?
✅ Good friction uses kiosk mode, app constraints, enforced updates
❌ Bad friction is breakable or inconsistently applied
5. Do you compare what should be happening to what actually is?
✅ Good friction detects and resolves drift
❌ Bad friction reviews configs after the damage is done
Conclusion: Solving the Zero-Trust Paradox
Good security isn't about more policies or more verification. It's about trust — through the intelligent application of friction.
The zero-trust paradox isn't a bug; it's a feature. By acknowledging that even "never trust, always verify" systems require human trust to function, we can build security that people actually use. If your teams feel like they're jumping through hoops with no clear reason, they'll find ways to circumvent them, and your controls will crumble under the weight of managing workarounds. But if your friction is intentional, transparent, and aligned to risk? It becomes part of how people work, not something they work against.
Security should never feel like a tax on productivity. It should feel like a seatbelt — invisible until it's needed, not like a straightjacket you put on every morning, and always there when it matters. Zero-trust handles the technical verification, but only trust can handle the human element. If your system isn't built on both, no amount of tooling will save it.
Start with trust. Use friction with purpose. And give your teams the clarity they need to stay safe and fast.
Look at your highest-friction security control today. Ask yourself: Is it building trust or teaching circumvention? Start there.

.avif)
